Security Posture
Ironholm AI is designed to support organizations with strict confidentiality, security, and regulatory requirements. The system architecture prioritizes data isolation, minimized attack surface, and operational predictability.
Security controls are implemented at the architectural level to reduce reliance on user configuration, operational procedures, or external service assurances.
Architecture Overview: Zero‑Network by Design
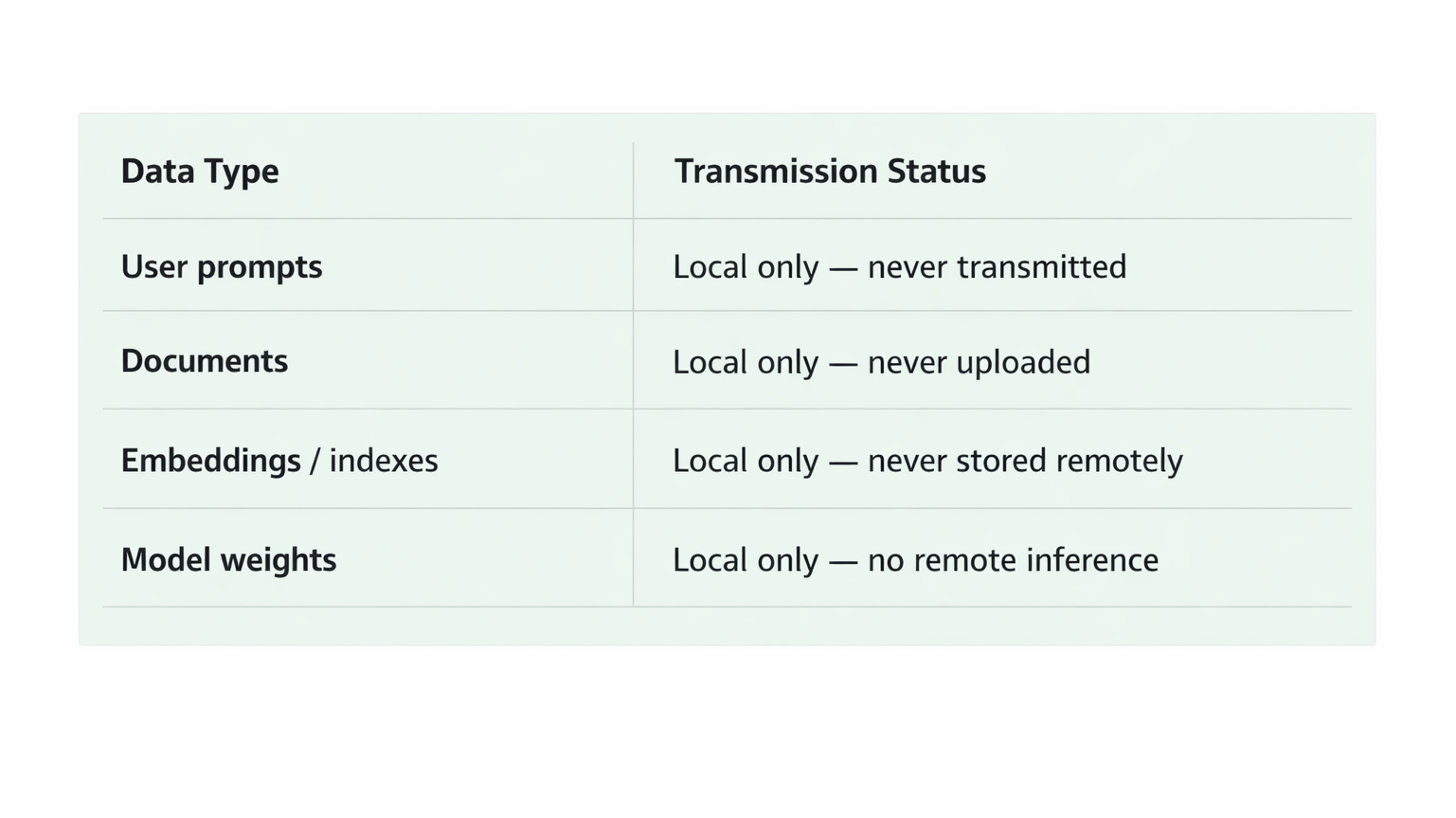
Ironholm AI uses a zero‑network architecture by default.
Core AI functionality operates entirely within the customer’s local environment. During normal operation, the system does not require network connectivity or access to external services.
Data isolation is structural, meaning:
- AI processing does not depend on cloud services
- Sensitive data is not transmitted outside the environment
- Security posture does not change based on configuration options
This approach limits exposure associated with network‑dependent systems and simplifies boundary definition for security review.
Threat Model Scope and Exclusions
Ironholm AI’s architecture is designed to eliminate reliance on external data processing paths. As a result, certain categories of risk are outside the system’s threat model.
The following vectors are not applicable to normal operation:
- Cloud storage exposure
The system does not upload or store customer data in external cloud environments. - Network‑based interception risks
No data transmission is required for AI processing under standard operation. - Third‑party data processor dependency
AI execution does not rely on external vendors, APIs, or shared processing infrastructure. - Cross‑border data transfer considerations
Data residency remains within the customer‑controlled environment. - External credential exposure
Operation does not require API keys or third‑party service credentials.
By removing these dependencies, Ironholm AI reduces the number of external controls required to manage residual risk.
Air‑Gap and Offline Operation
Ironholm AI supports deployment in restricted and offline environments, including air‑gapped systems.
- Pro and Max tiers support offline operation.
- Pro tier performs a periodic license validation approximately every 14 days.
- License validation does not transmit user data
- No document content or metadata is shared
- Max tier operates without any network connectivity requirements.
This design supports environments with limited or prohibited external network access.
Data Handling and Control
Ironholm AI does not retain, transmit, or process customer data outside the local environment. Data remains under customer control throughout system operation.
There is no use of customer data for:
- Model training
- Service improvement
- Third‑party processing
This simplifies data flow analysis and supports internal compliance and audit review processes.
Applicability to Regulated Environments
Ironholm AI is designed to support organizations that require:
- Strict data handling controls
- Predictable system behavior
- Clear security boundaries
- Reduced reliance on third‑party assurances
The architecture enables organizations to evaluate security posture based on system design rather than vendor policy claims.
Summary
Ironholm AI’s security approach emphasizes containment, isolation, and minimized dependency.
- Local execution by default
- No required cloud services
- No external data processing paths
- Clear, auditable system boundaries
Security is enforced through system design rather than operational configuration.